python代写哪里找的价位便宜?代写Python的通过率高不高?
1305python代写哪里找的价位便宜?代写Python的通过率高不高? python代写 随着人们生活水平的提高,人们的精神追求也在逐步的提高。对于出国留学都有了新的认识有了很高的思想觉悟,不再有人认为出国留学就是有钱...
View detailsSearch the whole station
物理攻击与对策代写 Please complete this assignment (100 pts total) and submit your report/program code on Canvas (all files compressed in one .zip without the .csv
Please complete this assignment (100 pts total) and submit your report/program code on Canvas (all files compressed in one .zip without the .csv file)
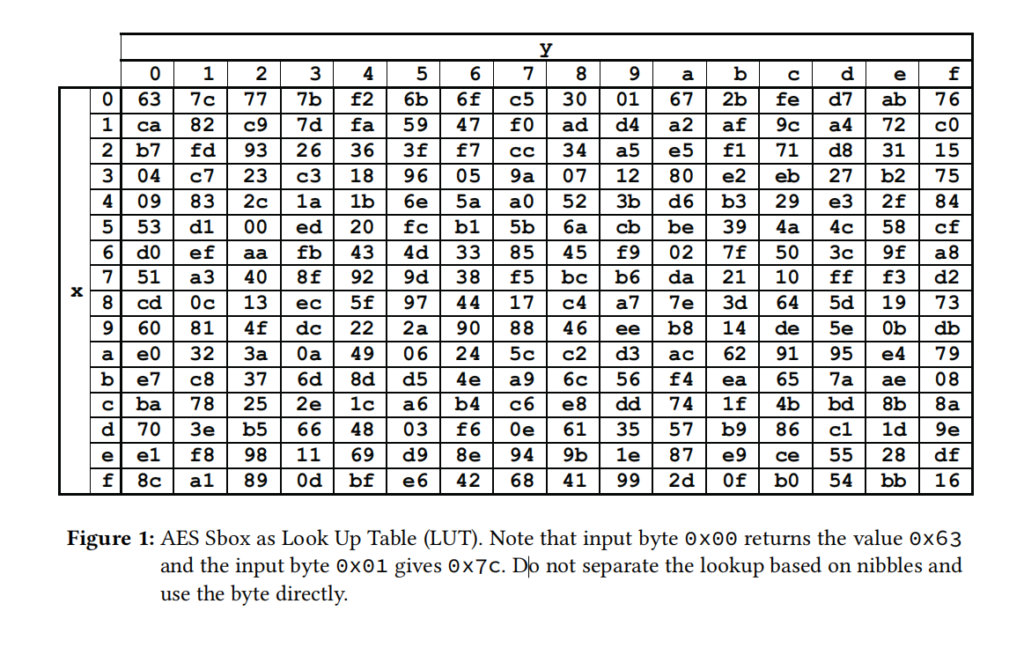
Please consider the following AES inputs and compute the output after the first SubBytes operation. Only use a pocket calculator and the table given in Figure 1. This is intended to make sure you fully understood the concept. (10 pts)
Plaintext = 00 00 00 00 00 00 C1 A5 51 F1 ED C0 FF EE B4 BE
Key = 00 00 01 02 03 04 DE CA F0 C0 FF EE 00 00 00 00
Note: FIPS 197 Appendix B is always a great reference for this kind of task∗ .
∗ https://nvlpubs.nist.gov/nistpubs/fips/nist.fips.197.pdf
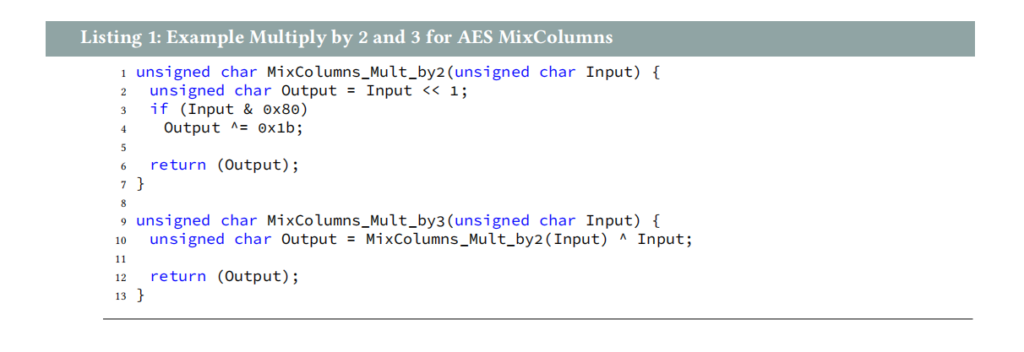
Your coworker needs to implement the AES MixColumns operation in software. He found some code on stackexchange.com. You remember the best practice to review (and test) code before using it in production. Therefore, you offer to review the code. (10 pts)
a) What is the type of problem here? (2 pts)
b) Identify the function(s) with undesired behavior. (2 pts)
c) Suggest a code fragment that solves the problem under idealized assumptions. (4 pts)
d) Is your solution processor independent? Please provide appropriate reasoning. (2 pts)
The file timing_noisy.csv contains 1 million timing samples of the AES with random plaintexts and a fixed key. This is representative for an actual attack scenario, as the attacker controls the input but not the key. The file format is .csv (Comma-Separated Values) and you should be able to read it in your preferred environment or convert it to any format that you need. Its first 16 columns contain the plaintext bytes in ASCII (from 0 to 255) and the last column shows the timing value. Your duty is to perform a timing side-channel analysis.
a) Recover the key. Please assume that the Most Significant Bit (MSB) is a good hypothesis. Provide figures to support that you found the correct key. (40 pts) 物理攻击与对策代写
b) Check how many samples you need for each key byte. This can be done, e.g., in 1 000 step increments and does not need to be an exact number. (20 pts)
c) Optimize your code such that the overall attack time (without incremental steps) is well below 3 Please report your execution time in addition to your processor and memory specification. Include a note which operating system you used. If you needed to optimize your code to improve runtime, briefly include a note how you optimized. (20 pts)
Please write your program in one of the following languages/environments: Python/Jupyter (strongly recommended), C/C++, Java, Rust, Matlab/Octave. Choose wisely, as you may be able to reuse code in follow-up assignments. Your .zip file should contain your code, instructions how to make it run (if needed), the figures, and the number of required samples.

更多代写:Cs代写作业合法吗 多邻国保分 英国assignment是论文吗 英国硕士论文选题 simpletense代写 线性代数作业代写
合作平台:essay代写 论文代写 写手招聘 英国留学生代写
python代写哪里找的价位便宜?代写Python的通过率高不高? python代写 随着人们生活水平的提高,人们的精神追求也在逐步的提高。对于出国留学都有了新的认识有了很高的思想觉悟,不再有人认为出国留学就是有钱...
View detailspython code代写会不会是直接抄袭的其他源代码?怎么检验? python code代写 计算机程序的学习非常有用,能够做很多的工作,比如软件工程师、网络安全工程师等,国外的计算机行业也非常发达,去国外高校深造...
View detailsdata1x02 Project 数据科学代写 Submission 1: Report Submit a written report on your work, as a PDF document. • This should be submitted through the link in the Canvas site. Submission 1: Repo...
View detailsCSC 445 Homework 2 (version 1) 算法设计代写 The questions are drawn from the material in Chapters 3, 4, and Appendix A of the text, and the lectures in class on asymptotics, sums, recurrences,...
View details