计算机体系结构cs代写 I218代写 计算机体系结构作业代写
597I218 Computer ArchitectureReport 3 计算机体系结构cs代写 (1) In the textbook and lecture slides, detailed information in the pipeline registers (IF/ID, ID/EX, EX/MEM, MEM/WB) is not provided. ...
View detailsSearch the whole station
计算机网络安全代写 INSTRUCTIONS This assignment has two parts. Make sure you read the instructions carefully. Part 1: WLAN Network Design and Security
| Purpose | In Part 1 of this assignment, students will record data from a real-world wireless network and demonstrate that they can analyse it, identify its properties and potential issues. In Part 2, students analyse Internet traffic and identify servers, clients and protocols used. The assignment is related to Unit Learning Outcomes 5 and 6. |
| Your task | You need to submit a report with your findings regarding the analysis tasks for Part 1. The instructions below contain concrete questions you should answer in your report. Part 2 is submitted via a Moodle quiz. |
| Value | 30% of your total marks for the unit The assignment is marked out of 60 marks. |
| Word Limit | 600 words for Task 1.2, no word limits for the remaining tasks |
| Due Date | 11:55 PM Friday 14 October 2022 计算机网络安全代写 |
| Submission | ● Via Moodle assignment submission (Part 1) ● Turnitin will be used for similarity checking of all submissions. ● Via Moodle quiz submission (Part 2) |
| Assessment Criteria | See rubric |
| Late Penalties | ● 10% deduction per calendar day or part thereof for up to one week ● Submissions more than 7 calendar days after the due date will receive a mark of zero (0) and no assessment feedback will be provided. |
| Support Resources | See Moodle Assessment page |
| Feedback | Feedback will be provided on student work via: ● general cohort performance ● specific student feedback ten working days post submission |
INSTRUCTIONS
This assignment has two parts. Make sure you read the instructions carefully.
For this part of the assignment, you will perform a real-world WLAN site survey. Your task is to produce a map of (part of) a building that gives an overview of the wireless networks that are available, as well as an analysis of the network.
What you will need: a WiFi-enabled laptop (some smartphones also work, see below), and a place to scan. For example, you can perform a survey of your home, of an office space, of parts of the Monash campus. If you don’t own a suitable device that you could use for this activity, try to borrow one from a friend, or contact us to figure out an alternative.
You have to complete two tasks (a survey and a report).
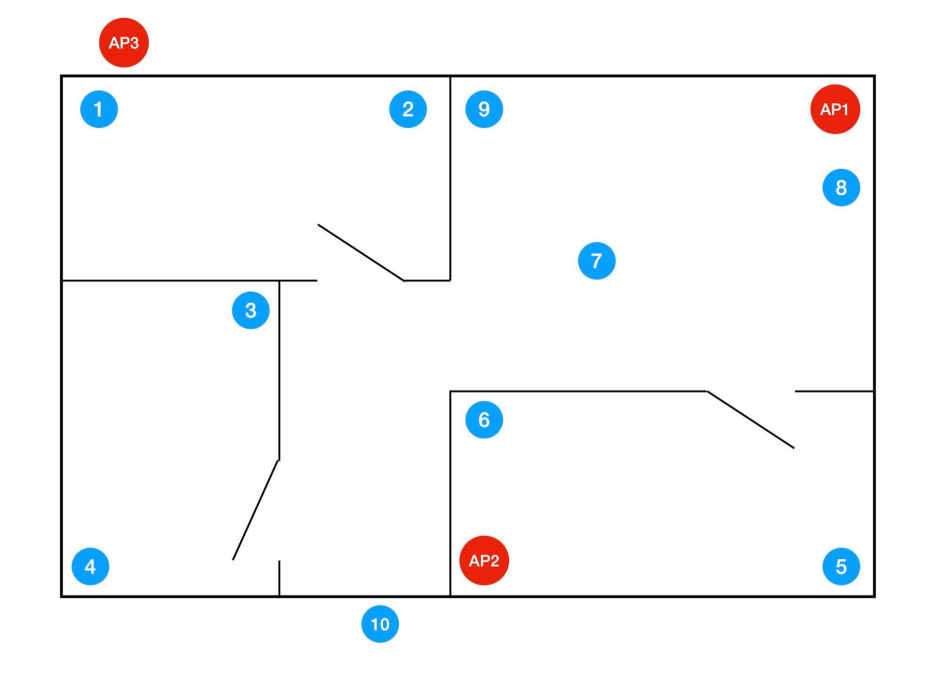
Create a map1 of the place you want to survey. A simple floorplan will be sufficient, it doesn’t have to be perfectly to scale. See the appendix for an example. The map needs to include distances and needs to be labelled with all relevant information (e.g. wall material, if used for the discussion). Your survey should cover an area of at least 60 square metres (e.g. 6×10 metres, or 4×15, or two storeys of 6×5 each). Be creative – the survey can include hallways or outside areas. Be sure to take the analysis in Task 1.2 into account, by designing your survey to include walls, doors etc. it will be easier to write something interesting in Task 1.2.
1 An example map is given in the Appendix. You may use any drawing tool to create a map (excluding heatmap generated by survey tools) or reuse exiting floor plan with reference.
Furthermore, your survey must include at least three WiFi access points. These can be your own, but can also include your neighbours’ APs or the ones at Monash, for example. If you are scanning in a commercial area or on campus, you should be able to see enough APs. If you want, you can create an additional AP with a phone (using “Personal hotspot” or “Tethering” features). 计算机网络安全代写
Depending on the scanning tool you use, you can record features such as the network name, MAC address, signal strength, signal to noise ratio (SNR), 802.11 version(s) supported, band (2.4 or 5 GHz) and channel(s) used.
Add the data gathered from the survey into the map of the covered area. On the map you should indicate the location of the access points and the locations where you took measurements.
For the access points, use the actual location if you know it, or an approximation based on the observed signal strength (e.g. if it’s your neighbour’s access point and you don’t know exactly where it is).
For each measurement point, you can either add the characteristics directly into the map, or create a separate table with the details. You can submit several maps if you choose to enter data directly into the maps, or a single map if you use additional tables. Create the map yourself, do not use the mapping features available in some commercial (i.e., paid) WLAN sniffing tools.
Write a report (word limit 600) on your observations analysing the data collected in the previous step (Task 1.1). Your analysis should investigate the following aspects:
● Channel occupancy: Are different access points competing on the same channels? Are they configured to use overlapping channels? Could the configuration be improved? (5 marks)
● Interference from walls, doors etc.: How do different materials affect signal strength and/or noise? Can you notice a difference in attenuation for different APs? (5 marks)
● Coverage: Do the access points sufficiently cover the desired area? Could the placement or configuration be improved? (5 marks)
● Any other aspect of your own choice. Here are a few suggestions: 计算机网络安全代写
○ measure the attenuation caused by your own body
○ measure the download and upload speeds in different locations
○ determine the overlap that has been implemented to enable roaming
○ describe how you interpolated the locations of access points from the signal strengths
Describe your findings and explain them with some technical detail (i.e., not only say what you found, but also how you performed the analysis or why you think the network is behaving that way). (5 marks)
Tools: You can use e.g. Acrylic Wifi (https://www.acrylicwifi.com/en/) for Windows, NetSpot (http://www.netspotapp.com) for macOS and Windows, and LinSSID or wavemon for Linux. If you have an Android smartphone, apps like Wifi Analyzer can also be used. On iOS, WiFi scanning apps do not provide enough detail, so iPhones won’t be suitable for this task. For drawing the site maps, any drawing tool should work, for example LucidChart, or even presentation tools such as PowerPoint, Keynote or Google Slides. Scans of hand-drawn maps are acceptable if they are neat and easily readable.
This part of the assignment requires you to download a PCAP file, open it in Wireshark and answer a few questions about the captured frames. The PCAP files are individualised, so make sure that you download the correct file while you are logged into Moodle.
You can access your individual PCAP file through the Assignment 3 Part B quiz link on Moodle. All of your answers have to be submitted via that Moodle quiz. You have two hours to complete the quiz after starting the attempt.
Here are a few tips on how to approach these tasks.
MAC addresses:
These are the addresses of individual devices at the Data Link Layer. Each frame contains a sender and receiver MAC address. For each frame, think about which device would be the sender and which the receiver.
IP addresses:
These are the Network Layer addresses. Remember that we use the DNS protocol to map a human-readable address (such as www.monash.edu) to an IP address (such as 202.9.95.188). So in order to find out the IP address for some of the devices, you may have to try to find DNS requests and responses in the PCAP file.
TCP connections:
Remember that each TCP connection starts with a three-way handshake. This was covered in the lectures, so you may have to go back to the videos if you’re not sure what those frames look like.
Hint: Please make sure you select the correct node (within your given scenario) for traffic analysis.
Appendix: Sample map

更多代写:加拿大cs网课代考 托福代考价格 英国Econ代上网课 英文essay必备万能句子 acm引用格式 海外大学网课
合作平台:essay代写 论文代写 写手招聘 英国留学生代写
I218 Computer ArchitectureReport 3 计算机体系结构cs代写 (1) In the textbook and lecture slides, detailed information in the pipeline registers (IF/ID, ID/EX, EX/MEM, MEM/WB) is not provided. ...
View detailsI218 Computer ArchitectureReport 2 cs计算机体系结构作业代做 (1)How is the instruction “sub $t9, $s4, $s7” translated to a machine instruction code? Answer the rs, rt, and rd fields in binary n...
View detailsEconomics 426: Problem Set 1 – Robinson Crusoe 经济问题集代做 I. Robin Crusoe is endowed with 112 labor-hours per week. There is a production function for the output of oysters Spring...
View detailsEconomics 426: Problem Set 8 – Production 经济学生产问题代写 I. Show that if A and B are closed subsets of Rn , then A+B is closed or provide a counter example. (20 pts) II. Show that if A and...
View details