高性能计算机架构代写 Computer Architecture代写
761ECE/CS 570 – High Performance Computer Architecture Homework #2 高性能计算机架构代写 1.Consider a shared-memory multiprocessor that consists of three processor/cache units and where cache co...
View detailsSearch the whole station
信息检索代写 Question 1. Choose concept(s) from below that are useful in discretionary access control. Explain their usefulness. (a) roles, (b) security classes,
Choose concept(s) from below that are useful in discretionary access control. Explain their usefulness. (a) roles, (b) security classes, (c) views, (d) statistical inference attack
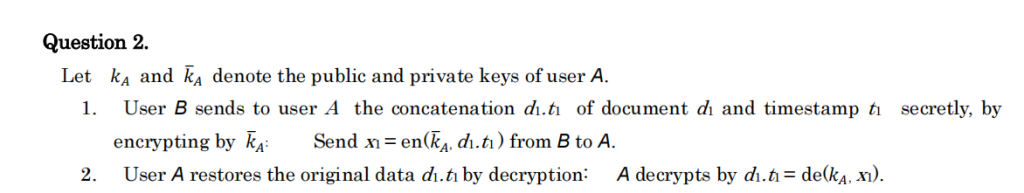
Using the notations above, describe two protocols that realize (1) and (2):
(1) User B signs document d2 with timestamp t2, and sends secretly to user A. User A checks whether the sent document has a valid signature of B.
(2) Both users A and B sign on document d3, and d3 is encrypted by some keys. User C should not see document d3, but C needs to check whether the signs by A and B are both valid.
Below (a)-(c) are schedules with symbols S(shared lock), X(exclusive lock), U(x) (unlock), Ab (abort), and Cm (commit). T1, T2, T3 are transactions.
(a) T1:X(A), T1:R(A), T2:X(B), T1:W(A), T1:U(A), T2:W(B), T2: U(B), T1:Co, T2:Co
(b) T1:X(B), T2:X(A), T1:R(B),T2:R(A), T2:S(B), T1:S(A),T2:R(B), T1:R(A), T1:W(B), T1:U(A), T1:U(B), T1:Co, T2:W(A), T2:U(A), T2:U(B), Co
(c) T1:X(A), T1:R(A), T1:W(A), T1:U(A), T2:X(A), T1:S(B), T2:W(A), T1:R(B), T2:U(A), T2:Co, T1:X(A), T1:W(A), T1:Co
(1) For each schedule of (a)-(c) above, choose all the properties from below that hold in the schedule. Also, briefly explain your answers.
1. RW-conflict, 2. WR-conflict, 3. WW-conflict, 4. conflict-serializable, 5. two-phase locking, 6. causing a deadlock, 7. avoiding cascading aborts, 8. view-serializable, 9. strict, 10. recoverable.
Here, a schedule is said to be strict if a value written by a transaction T is not read or overwritten by other transactions until T either aborts or commits. In a recoverable schedule, transactions commit only after all transactions whose changes they read commit.
(2) For statements (i) and (ii) below, argue whether each statement is true or not. Also show examples or counter-examples of schedules.
(i) Recoverable schedules are avoiding cascading aborts.
(ii) Two-phase locking protocol produces conflict-serializable schedules.
When inserting a value to a B+-index tree, node splits can happen. To keep consistency, nodes need to be locked. There are two algorithms such that (A) starts locking from the root node, and (B) starts locking from a leaf node.
1. Briefly explain node insertion algorithms (A) and (B).
2. Discuss advantages and disadvantages of (A) and (B).

1. Write the answers to the following XPath queries applied on d1.
(a) //car[option]/@color
(b) //*[@grade]/text()
(c) /*/*/option/ancestor::*/attribute::*
(d) /*/*/*/preceding-sibling::option
(e) //*[name()=’year’]/ancestor::*/name()
2. Write an XPath query which returns the following:
(a) Query which is equivalent to the query of 1.(c) and the query contains a qualifier.
(b) Return the maker of ‘car’ elements that have a ‘year’ element or ‘year’ attribute in its descendants, and the ‘year’ is greater 2016.
(c) Find ‘car’ elements that have two or more ‘option’ elements.
(d) Find elements q such that q has NO ancestor that has element name ‘special’.
(e) Simplest query which returns “Shuttle”, but the query must not include any element or attribute names in document d1.

更多代写:留学生CS exam帮考 gre网上代考 英国金融代上网课推荐 犯罪学论文代写 教育学论文写作 essay写作技巧代写
合作平台:essay代写 论文代写 写手招聘 英国留学生代写
ECE/CS 570 – High Performance Computer Architecture Homework #2 高性能计算机架构代写 1.Consider a shared-memory multiprocessor that consists of three processor/cache units and where cache co...
View detailsAssignment – 11 [ 100 Points ] CSC-220-06 Data Structures 数据结构代写 Assignment Goals Answer the following questions. Points applicable for each of the questions are mentioned along...
View detailsI218 Computer ArchitectureReport 3 计算机体系结构cs代写 (1) In the textbook and lecture slides, detailed information in the pipeline registers (IF/ID, ID/EX, EX/MEM, MEM/WB) is not provided. ...
View detailsCSCI-570 Analysis of Algorithms Practice Exam - 2 算法分析代写 True/False Problems 1. For every graph G and every maximum flow on G, there always exists an edge such that increasing the ...
View details